One Platform for Complete Protection
CyberWall Shield provides strong security oversight and defense for your IT assets through its Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) features. Its use cases are tailored to protect your digital assets and bolster your organization’s cybersecurity stance.
Discover The Threat Shield Platform For Your Business
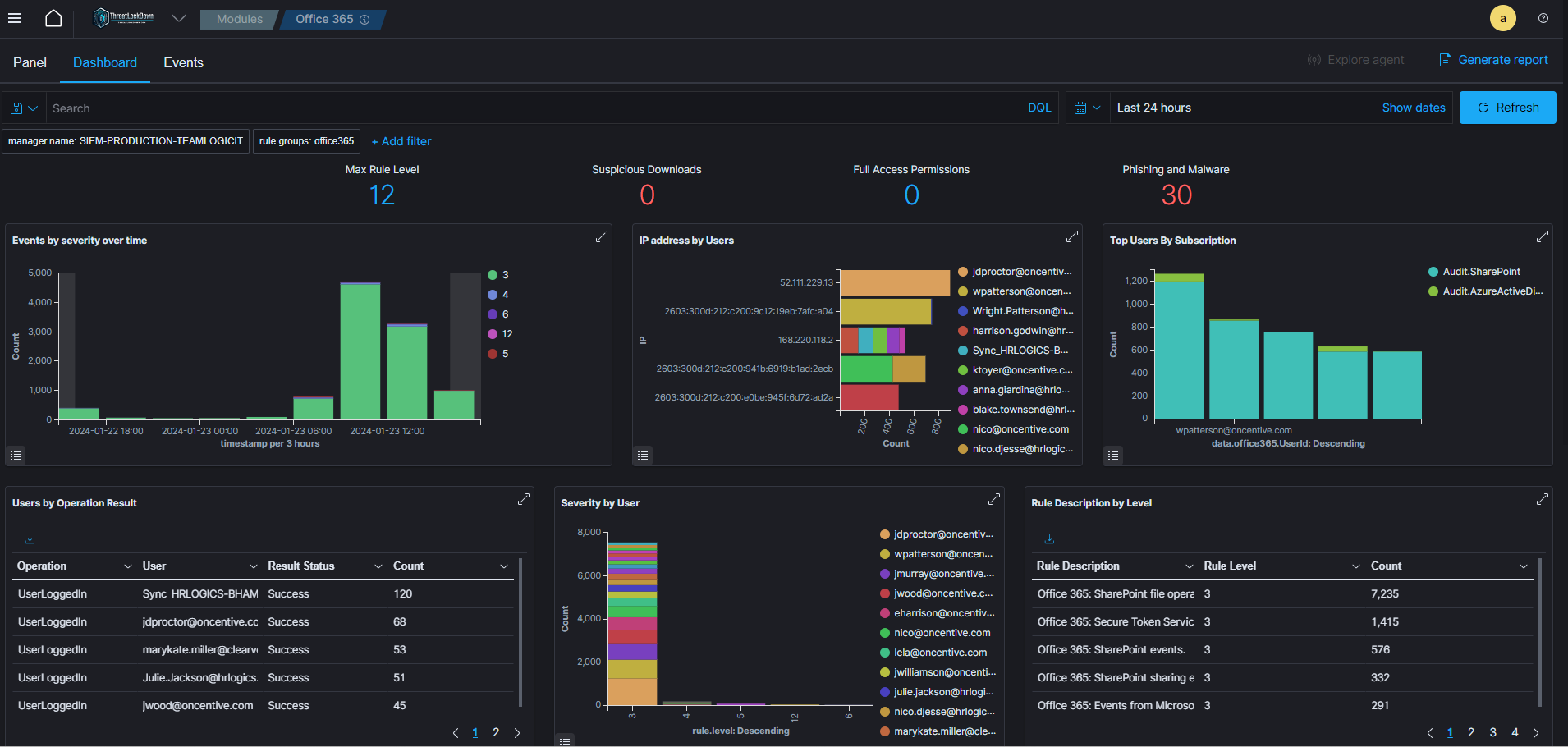
Office 365 Monitoring
CyberWall Shield excels in monitoring Office 365 environments for cyber threats, providing comprehensive protection against digital risks. It employs advanced analytics to continuously scan for suspicious activities, safeguarding against phishing, malware, and unauthorized access. By integrating seamlessly with Office 365, CyberWall Shield ensures real-time detection of anomalies and potential breaches, promptly alerting administrators to take swift action. Its robust capabilities include monitoring email traffic, analyzing login patterns, and tracking file movements, offering a layered defense mechanism. This vigilant surveillance is crucial in today’s landscape where Office 365’s widespread use makes it a prime target for cybercriminals.
Regulatory Compliance
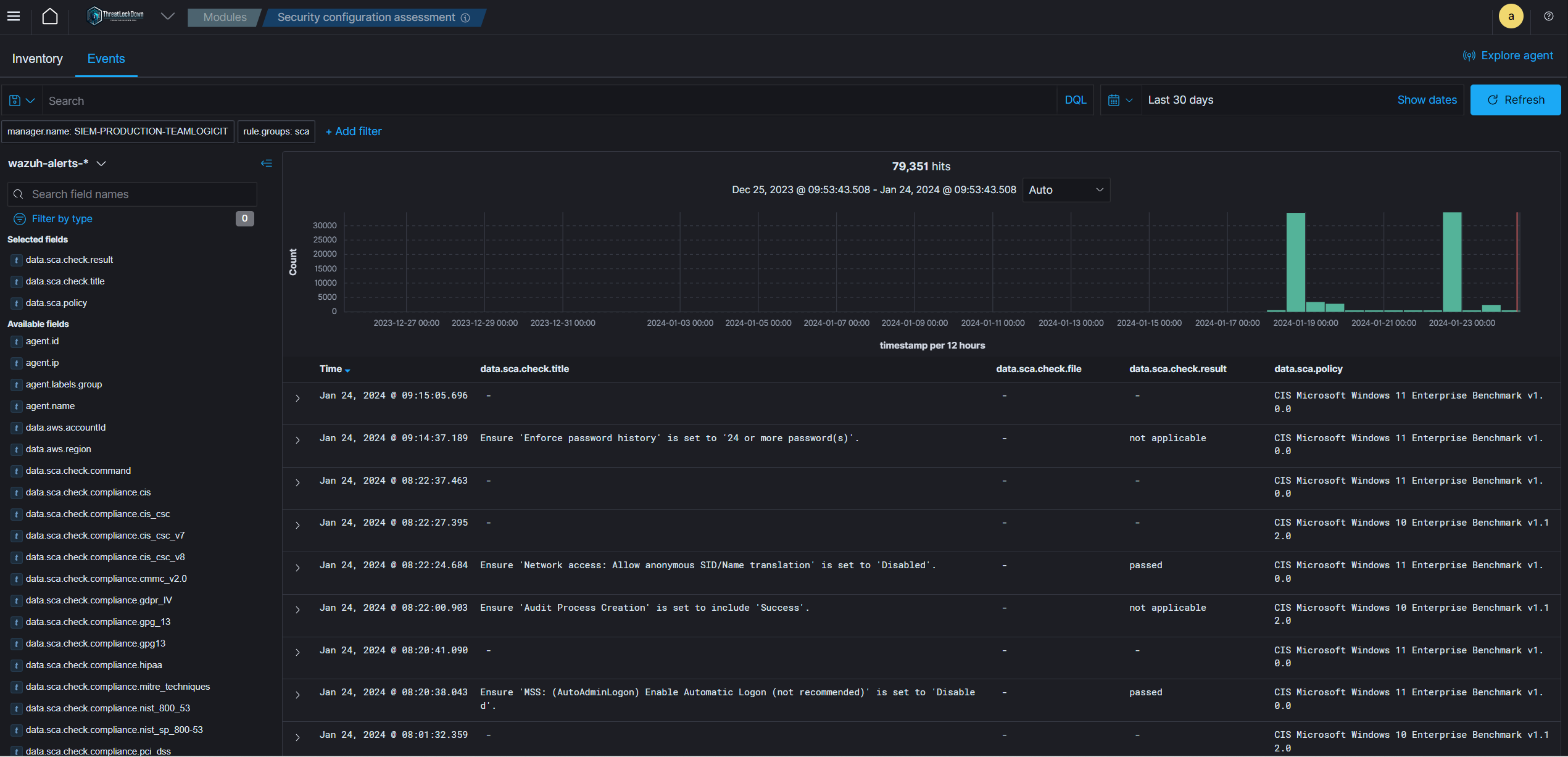
CyberWall Shield vigilantly oversees system and application configurations, verifying their adherence to your security policies, standards, and hardening guidelines. Its agents conduct regular scans to uncover any misconfigurations or vulnerabilities in endpoints that could be leveraged by attackers. Furthermore, these configuration assessments are customizable, allowing you to adjust them to fit your organization’s specific requirements. Security notifications come with suggestions for improved configurations, relevant references, and correlations with regulatory compliance standards.
CyberWall Shield offers essential security controls crucial for compliance with various industry standards and regulations. These controls encompass File Integrity Monitoring (FIM), Security Configuration Assessment (SCA), vulnerability detection, system inventory, among others. Its scalability and support for multiple platforms aid organizations in fulfilling technical compliance mandates. Additionally, CyberWall Shield generates reports and dashboards tailored for regulations like SOC 2, GDPR, NIST, TSC, and HIPAA, assisting in compliance management.
Malware Detection
CyberWall Shield identifies harmful behaviors and signs of compromise on endpoints, often due to malware infections or cyberattacks. Its ready-made ruleset and features such as Security Configuration Assessment (SCA), Rootcheck, and File Integrity Monitoring (FIM) are instrumental in spotting malicious actions and irregularities. These functions of CyberWall Shield can be adapted and configured to meet the unique needs of your organization.
Vulnerability Detection
Workload Protection
CyberWall Shield safeguards workloads in both cloud and on-premises environments. It seamlessly integrates with cloud services such as AWS, Microsoft Azure, GCP, Microsoft 365, and GitHub, enabling monitoring of services, virtual machines, and platform activities. Its centralized log management feature assists organizations utilizing these cloud platforms in maintaining compliance with regulatory standards.

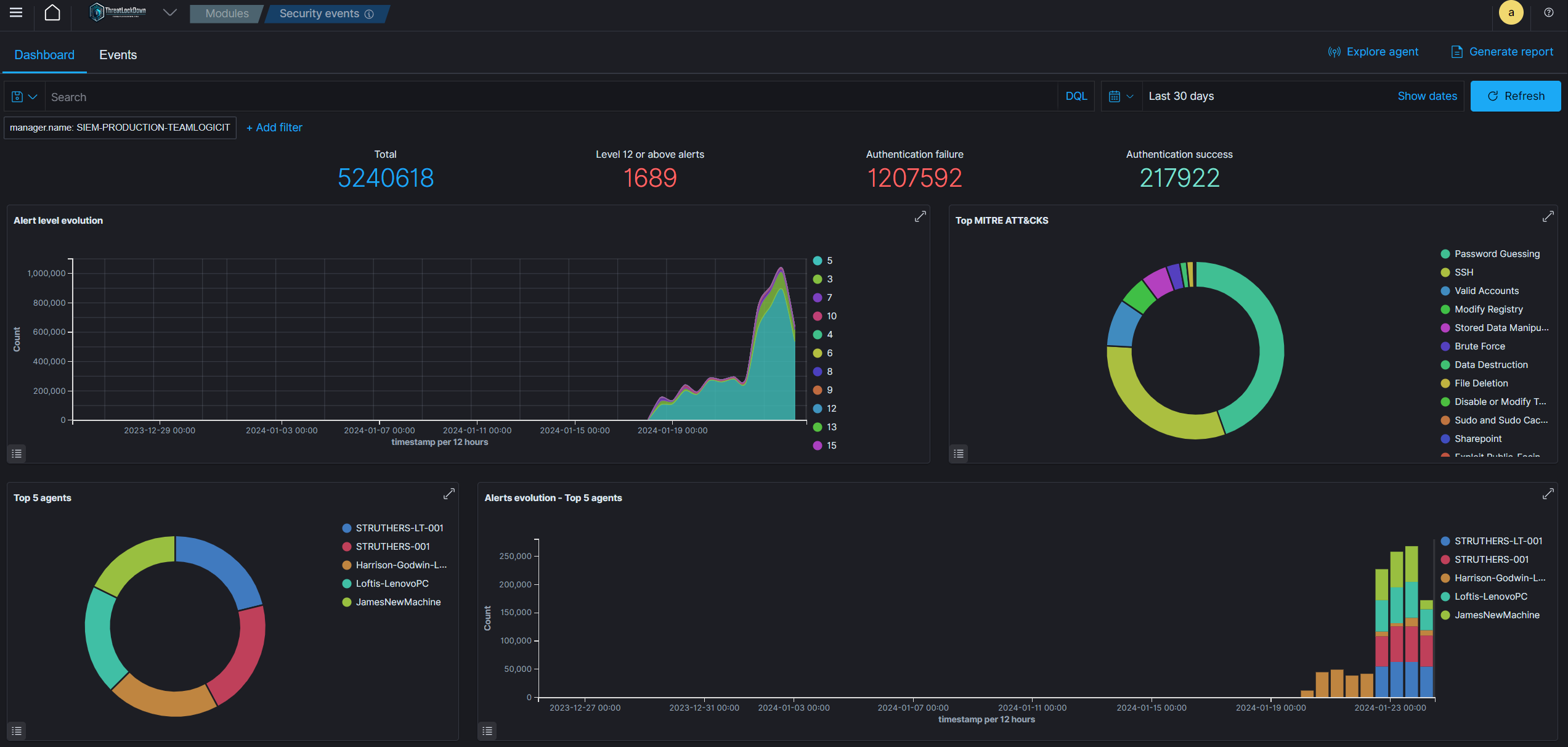
Incident Response
CyberWall Shield comes equipped with ready-to-use active responses designed to counteract active threats. Triggered upon specific conditions being met, these responses range from severing network access to an endpoint originating from a threat source, among other actions. Furthermore, CyberWall Shield enables remote execution of commands or system inquiries, detection of indicators of compromise (IOCs), and facilitation of incident response operations.
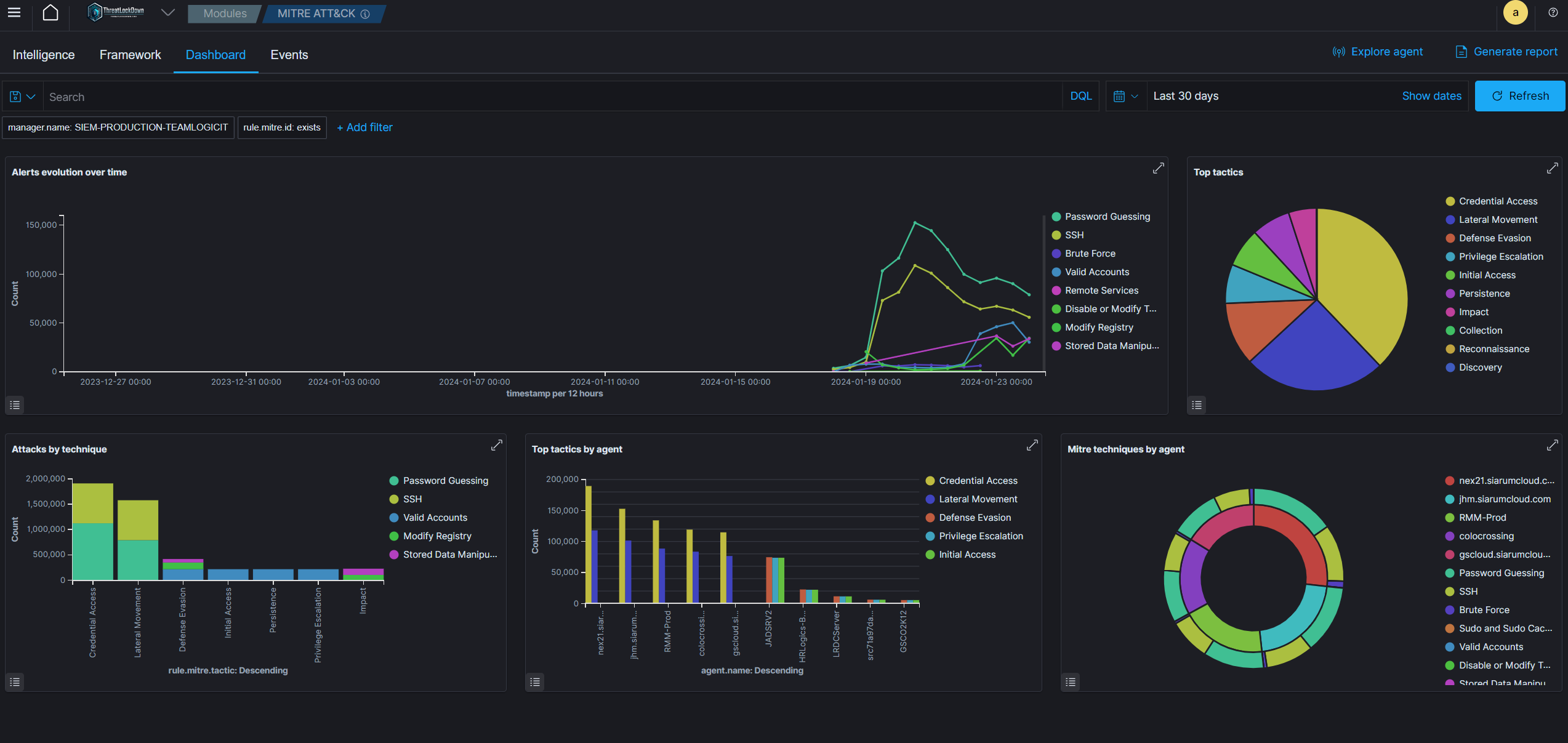
Log Data Analysis
CyberWall Shield agents gather logs from operating systems and applications and securely transmit them to the CyberWall Shield server, where they undergo rule-based evaluation and are archived. These rules within CyberWall Shield are designed to identify system or application errors, misconfigurations, harmful activities, breaches of policy, and a range of other security and operational concerns.
Containers Security
CyberWall Shield enhances security oversight for Docker hosts and containers by observing their activities and identifying potential threats, vulnerabilities, and deviations from the norm. With native integration into the Docker engine, the CyberWall Shield agent enables the monitoring of container images, storage volumes, network configurations, and active containers. It persistently gathers and scrutinizes in-depth runtime data, generating alerts for situations such as containers operating with elevated privileges, susceptible applications, the execution of a shell within a container, modifications to persistent storage volumes or images, among other security concerns, settings and even apply custom CSS to this text in the module Advanced settings.

Configuration Assessment
CyberWall Shield keeps a vigilant eye on system and application configuration settings to verify their alignment with your established security policies, standards, or hardening protocols. Its agents conduct regular scans to unearth any misconfigurations or vulnerabilities within endpoints that could serve as openings for malicious actors. Moreover, these configuration assessments can be personalized to fit the specific requirements of your organization. Security notifications come equipped with suggestions for enhanced configurations, pertinent references, and correlations to regulatory compliance standards.
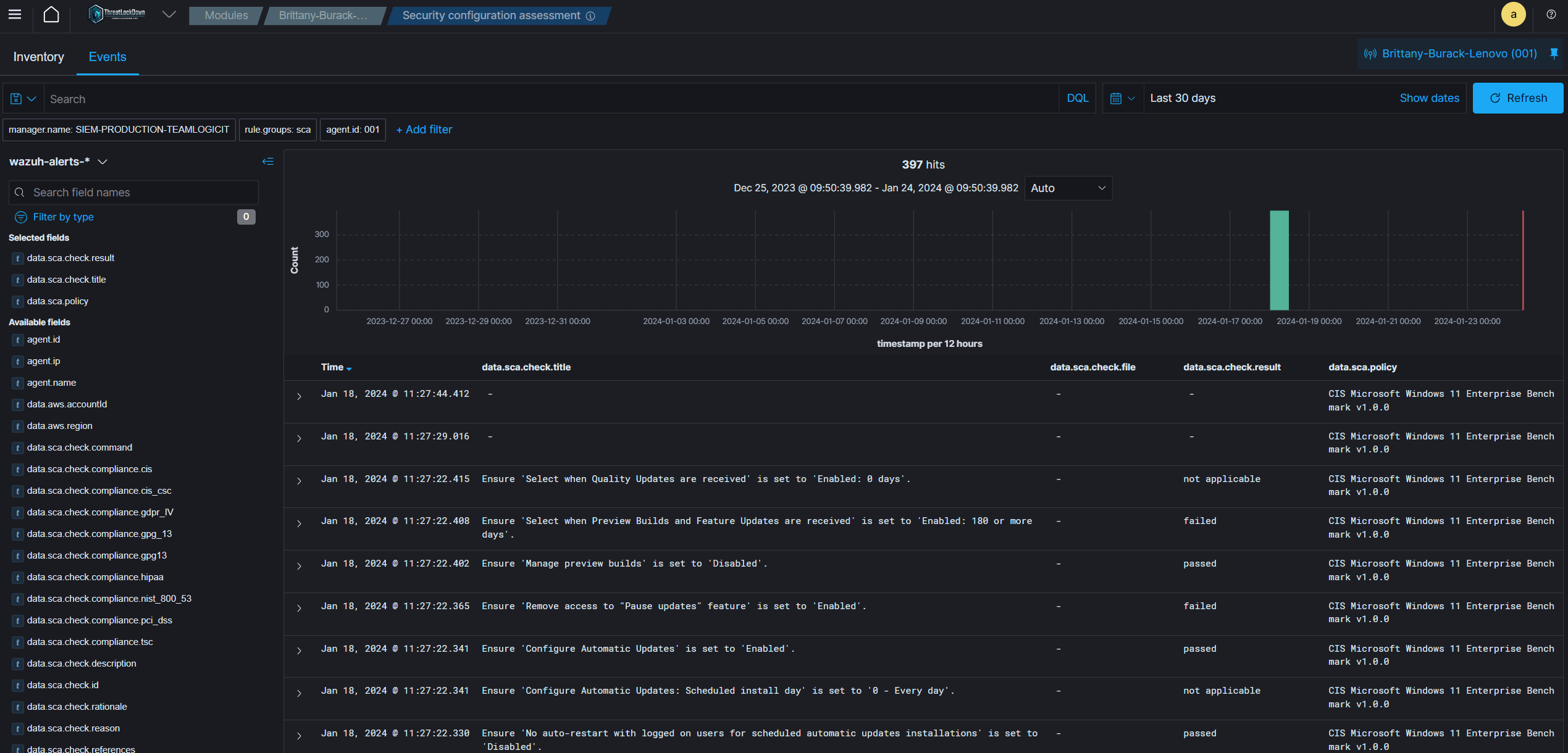
File Integrity Monitoring
CyberWall Shield oversees the file system, detecting alterations in content, permissions, ownership, and file attributes that require monitoring. It also inherently recognizes the users and applications responsible for file creation or modifications. Utilizing CyberWall Shield’s File Integrity Monitoring (FIM) feature alongside threat intelligence can aid in pinpointing threats or identifying compromised endpoints. Furthermore, FIM contributes to fulfilling various regulatory compliance requirements, including those set by PCI DSS, NIST, among others.
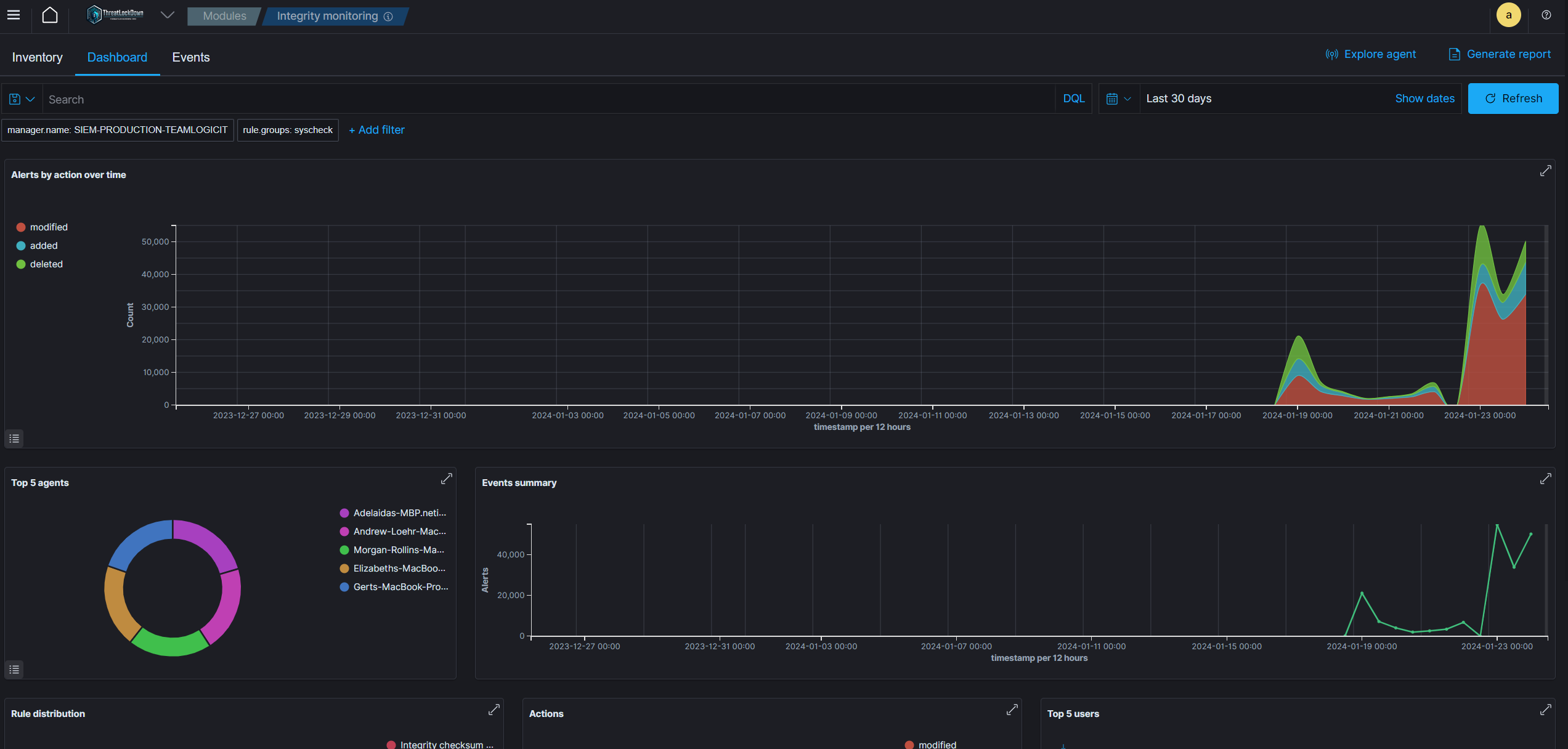
Threat Hunting
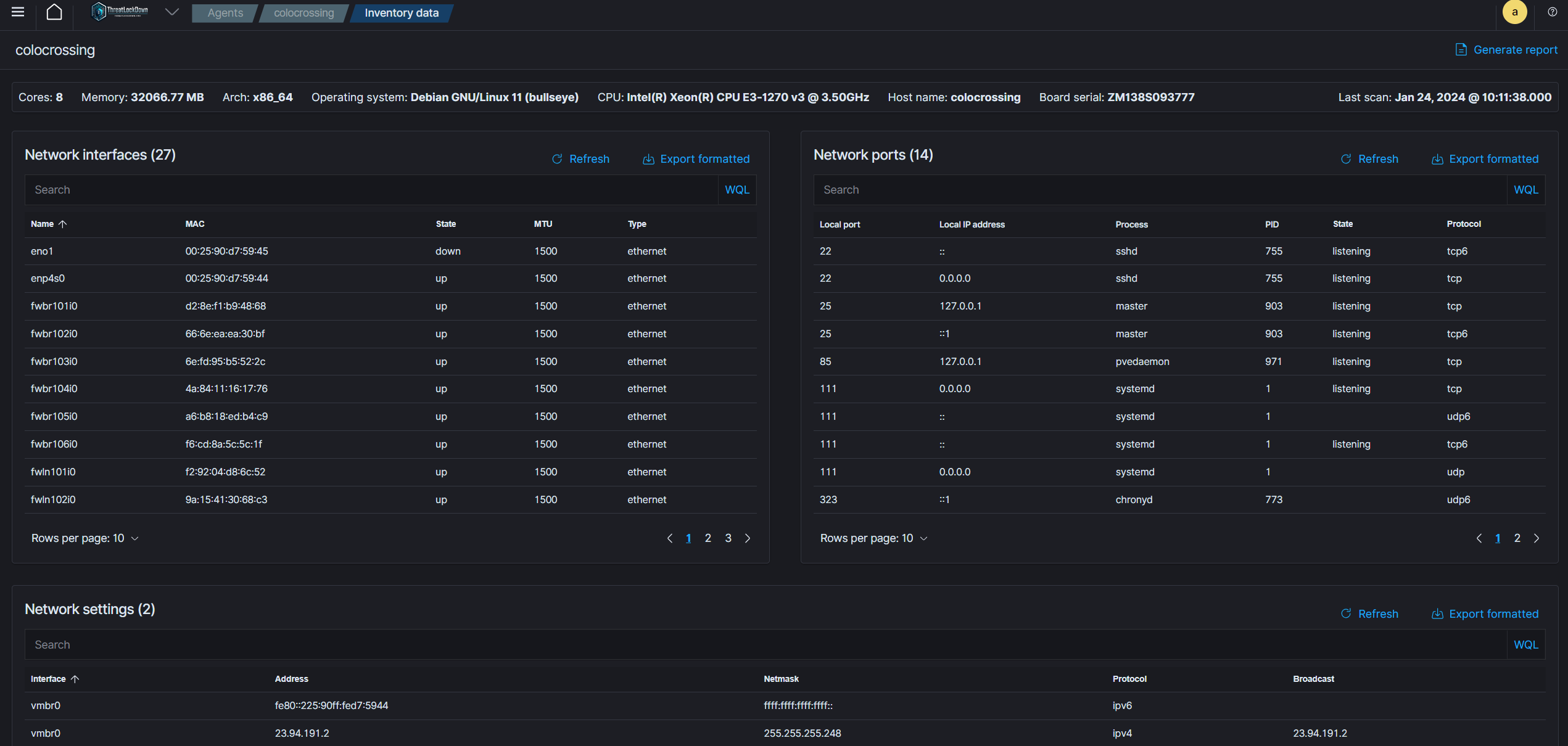
Inventory Data
CyberWall Shield creates a current inventory of all monitored endpoints, encompassing details such as installed software, active processes, open network ports, hardware specifics, and operating system data. Gathering this data enhances asset visibility and promotes effective IT management practices for organizations. Additional features of CyberWall Shield, including vulnerability identification, Security Configuration Assessment, and malware detection, contribute to safeguarding these endpoints and bolstering IT hygiene.
Posture Management
CyberWall Shield synchronizes with cloud platforms to gather and consolidate security-related information, issuing alerts for detected security threats and vulnerabilities to maintain security and ensure adherence to regulatory standards.

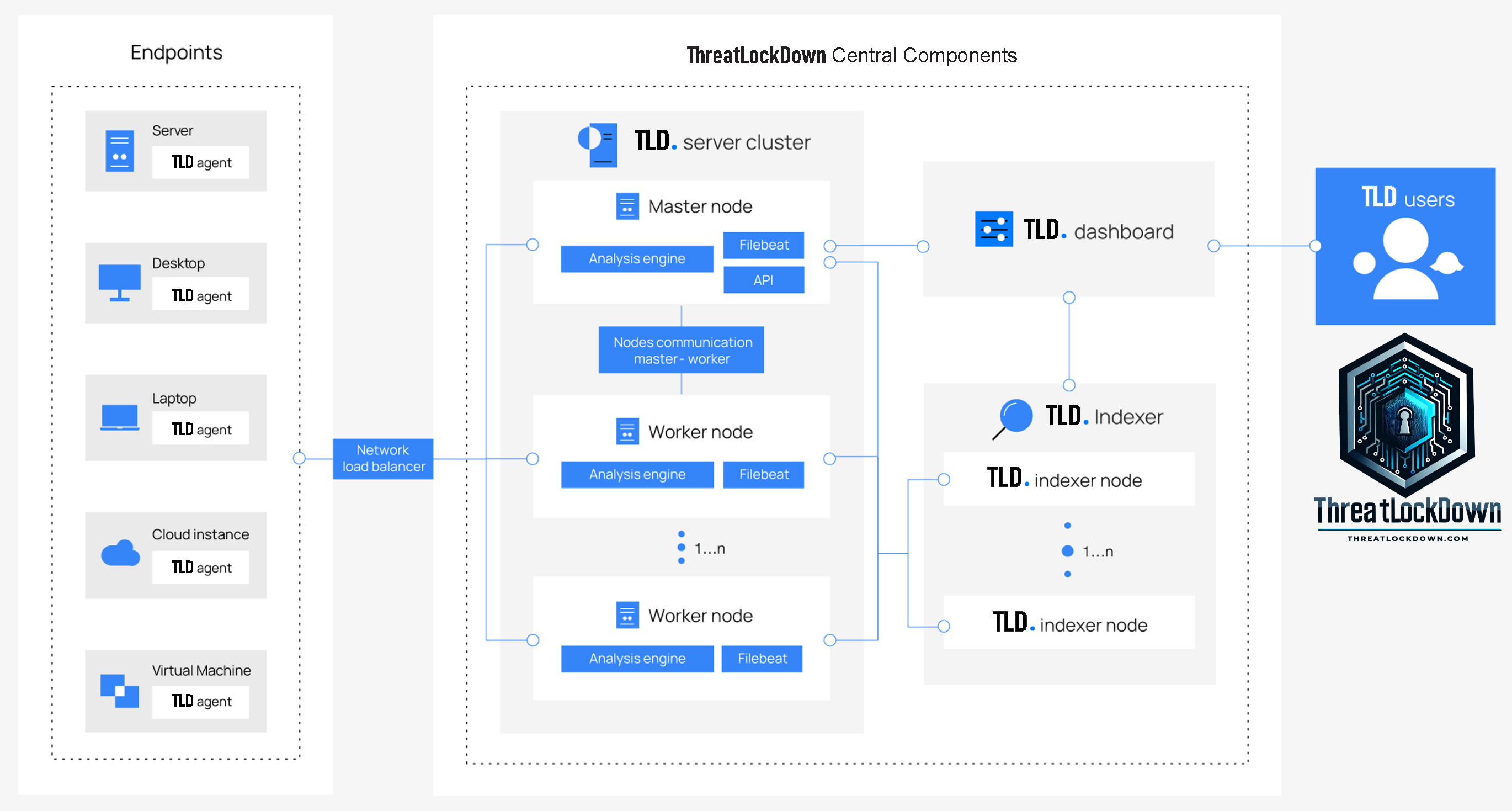
CyberWall Shield Central Components
CyberWall Shield Indexer
The CyberWall Shield indexer, a scalable full-text search and analysis engine, handles the indexing and storage of alerts produced by the CyberWall Shield server. Depending on environmental requirements, it can be set up as either a single-node or a multi-node cluster.
CyberWall Shield Server
The server oversees the agents, handling their remote configuration and updates as needed. It processes the data incoming from the agents by applying decoders and rules, and utilizes threat intelligence to search for indicators of compromise.
CyberWall Shield Dashboard
An adaptable and user-friendly web interface designed for data exploration, analysis, and visualization. This dashboard facilitates the management of CyberWall Shield settings and the monitoring of its operational status.
Discover CyberWall Shield, the all-in-one security & compliance platform
The single most secure cybersecurity platform that integrates SIEM, MDR and XDR capabilities in a unique solution.